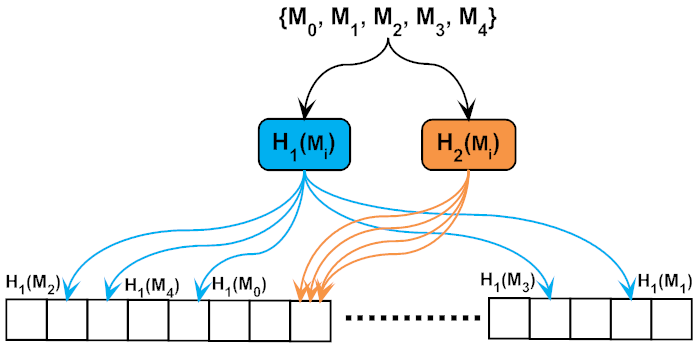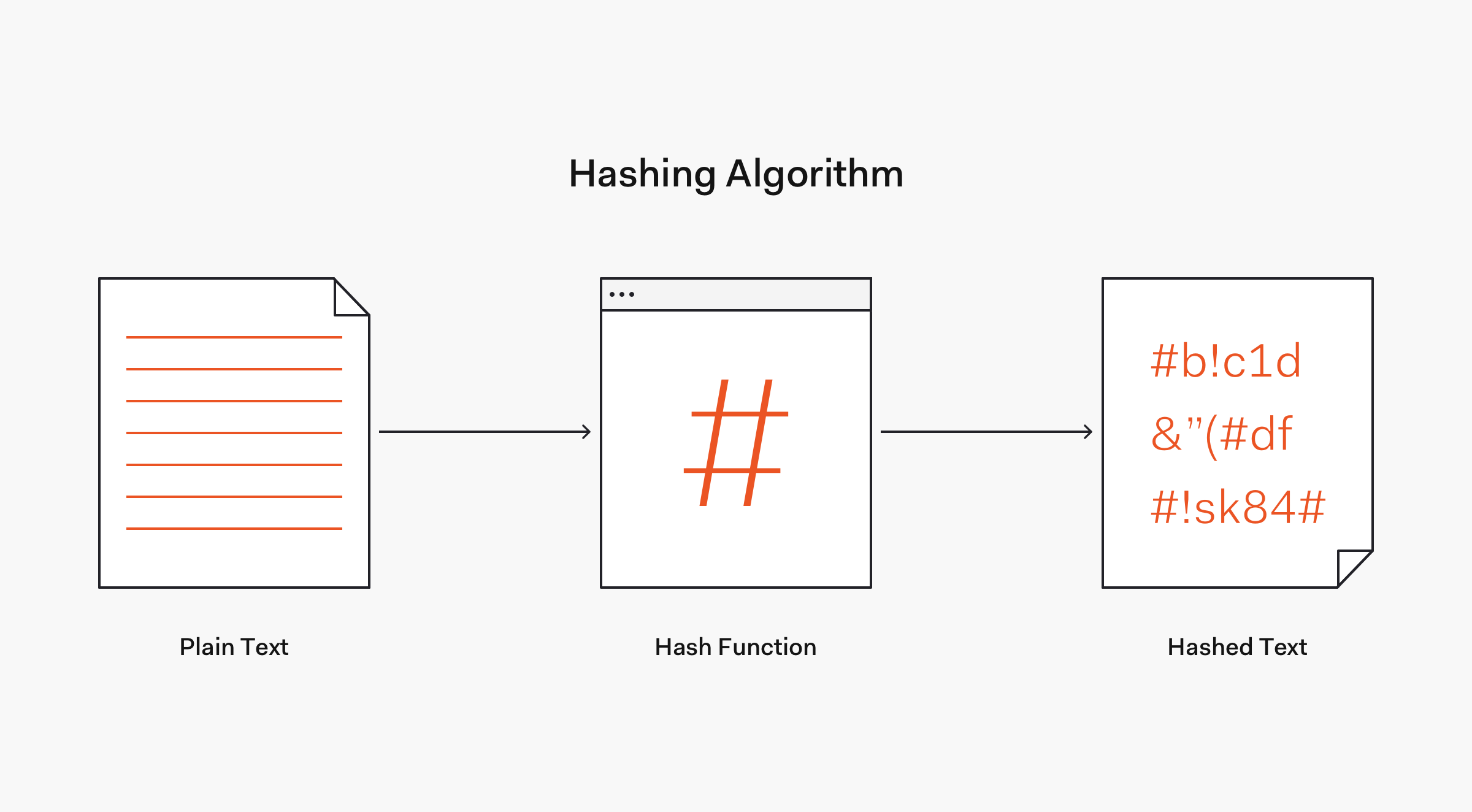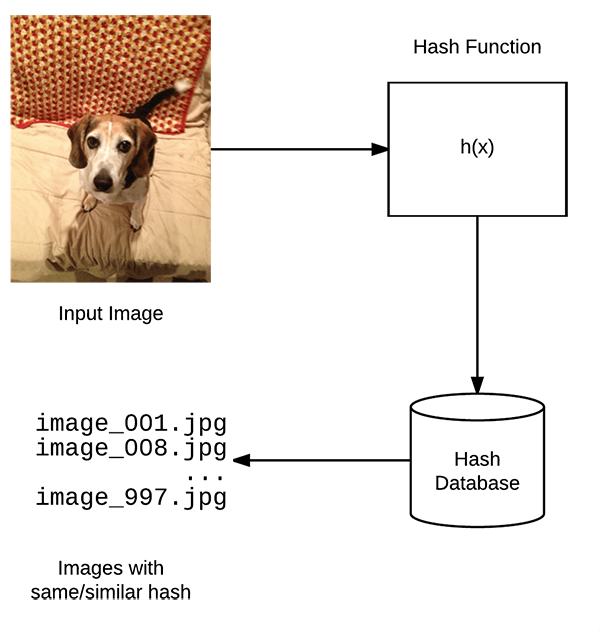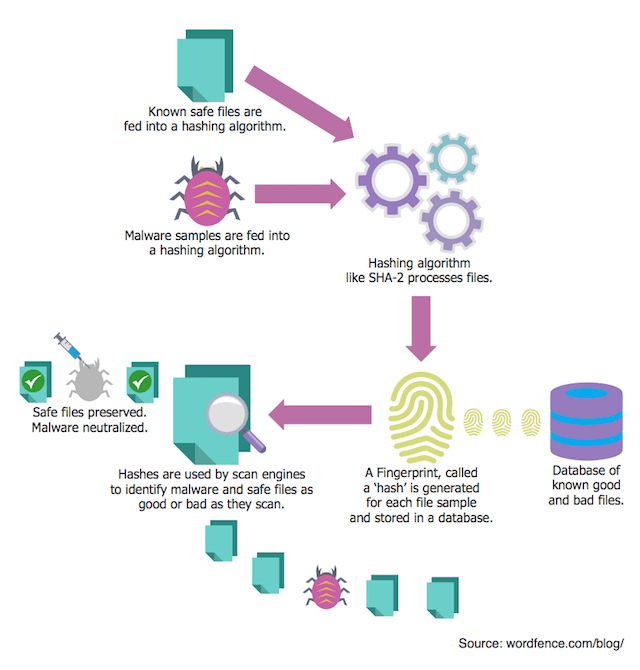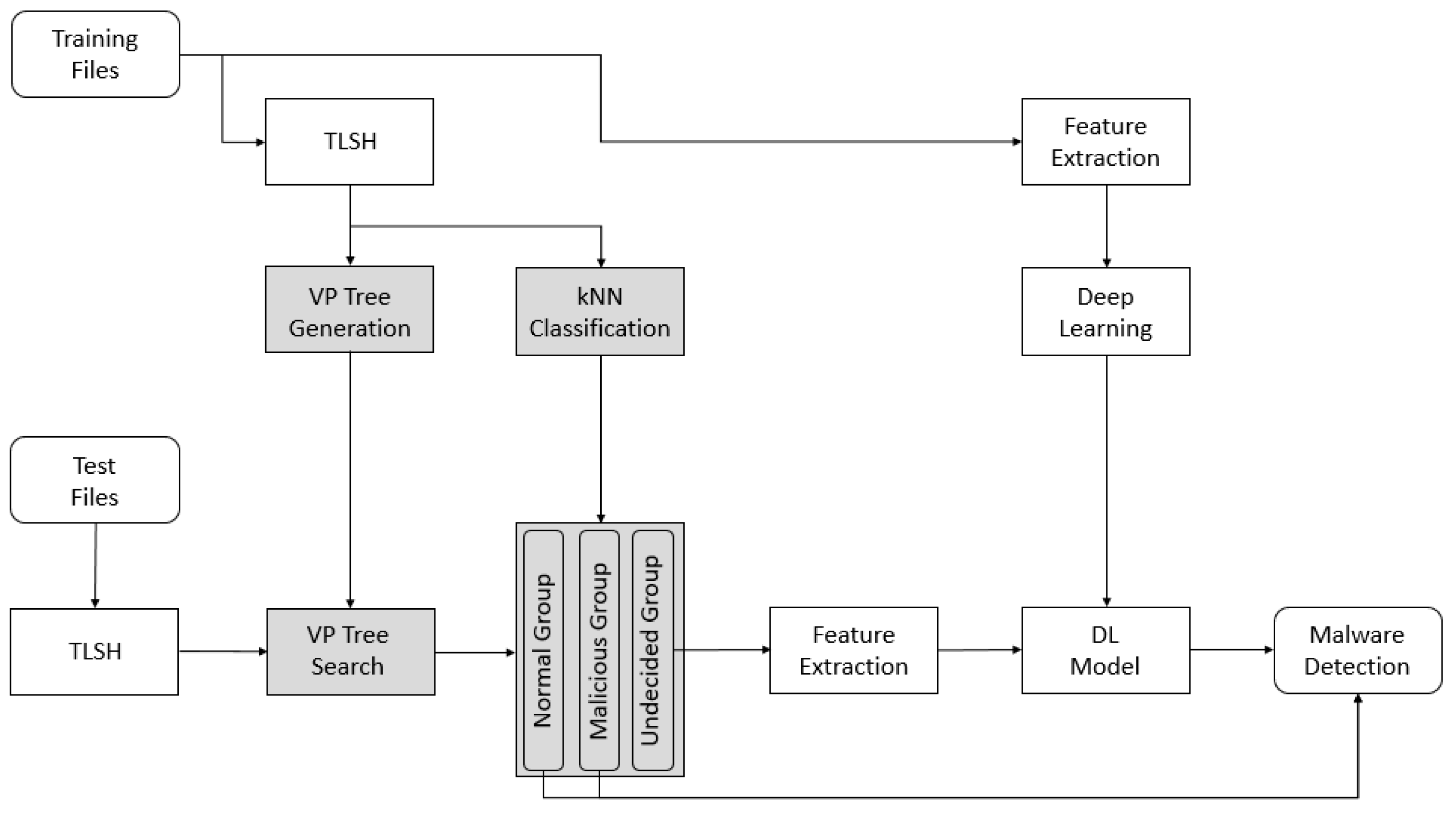
Applied Sciences | Free Full-Text | Combined kNN Classification and Hierarchical Similarity Hash for Fast Malware Detection
![PDF] Approach of Tamper Detection for Sensitive Data based on Negotiable Hash Algorithm | Semantic Scholar PDF] Approach of Tamper Detection for Sensitive Data based on Negotiable Hash Algorithm | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/8b154e7d16dddf63b49fe3fa05b7e7337f6824a4/3-Figure1-1.png)
PDF] Approach of Tamper Detection for Sensitive Data based on Negotiable Hash Algorithm | Semantic Scholar

Distributed anomaly detection and localization algorithm combined with... | Download Scientific Diagram

Water | Free Full-Text | Hash-Based Deep Learning Approach for Remote Sensing Satellite Imagery Detection
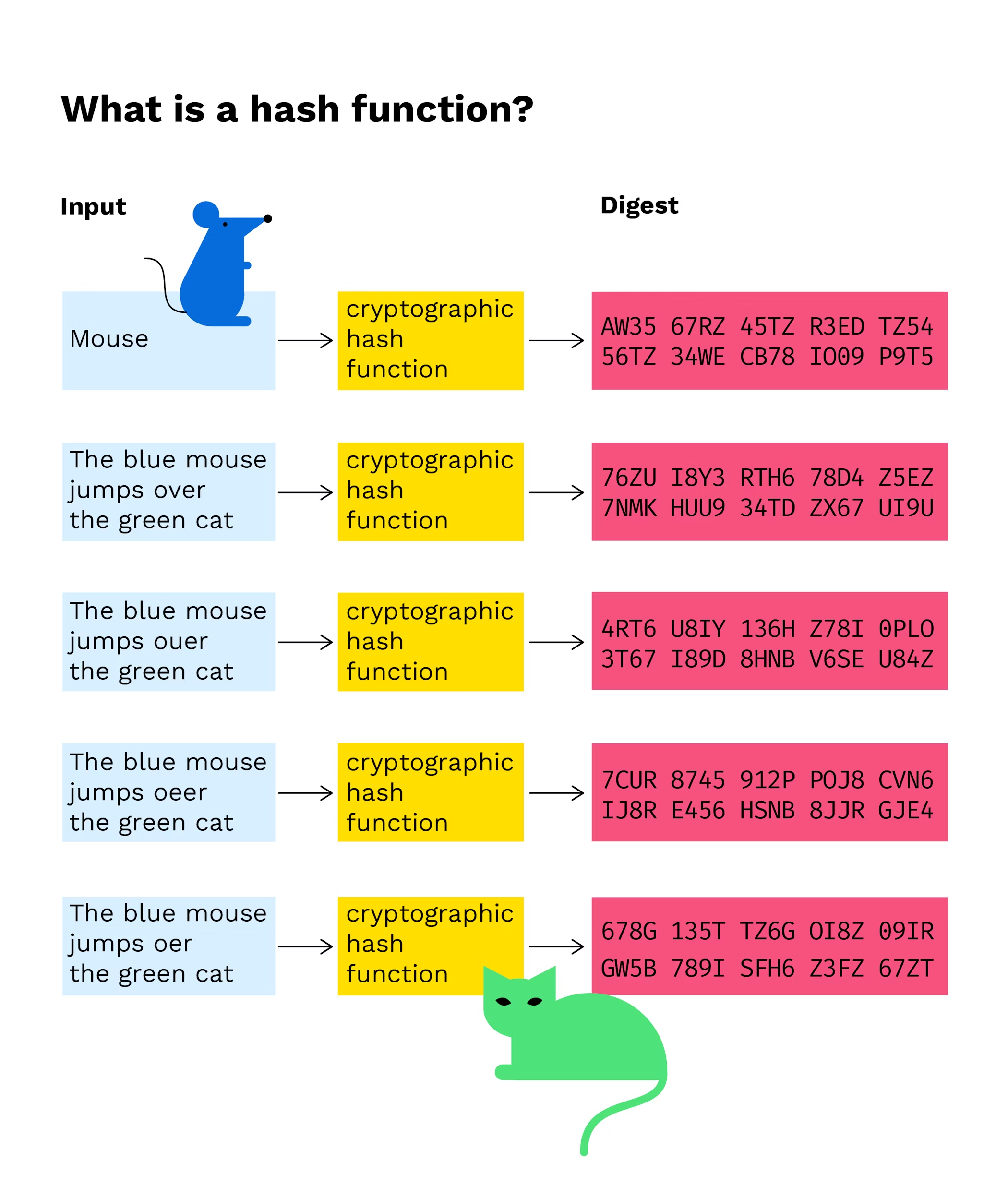


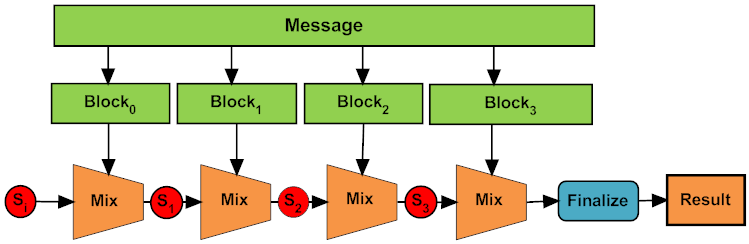


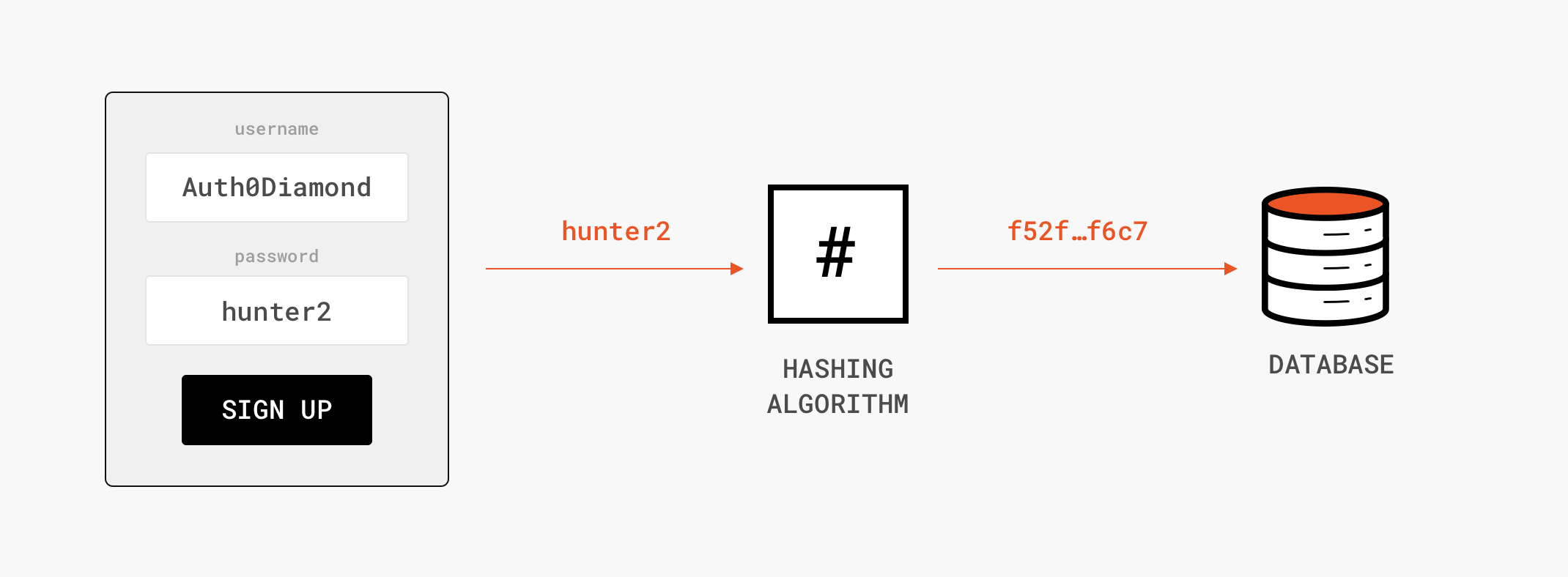
![What Is a Hash Function Within Cryptography [Quick Guide] - Security Boulevard What Is a Hash Function Within Cryptography [Quick Guide] - Security Boulevard](https://positiwise.com/wp-content/uploads/2022/06/hash-function.png)