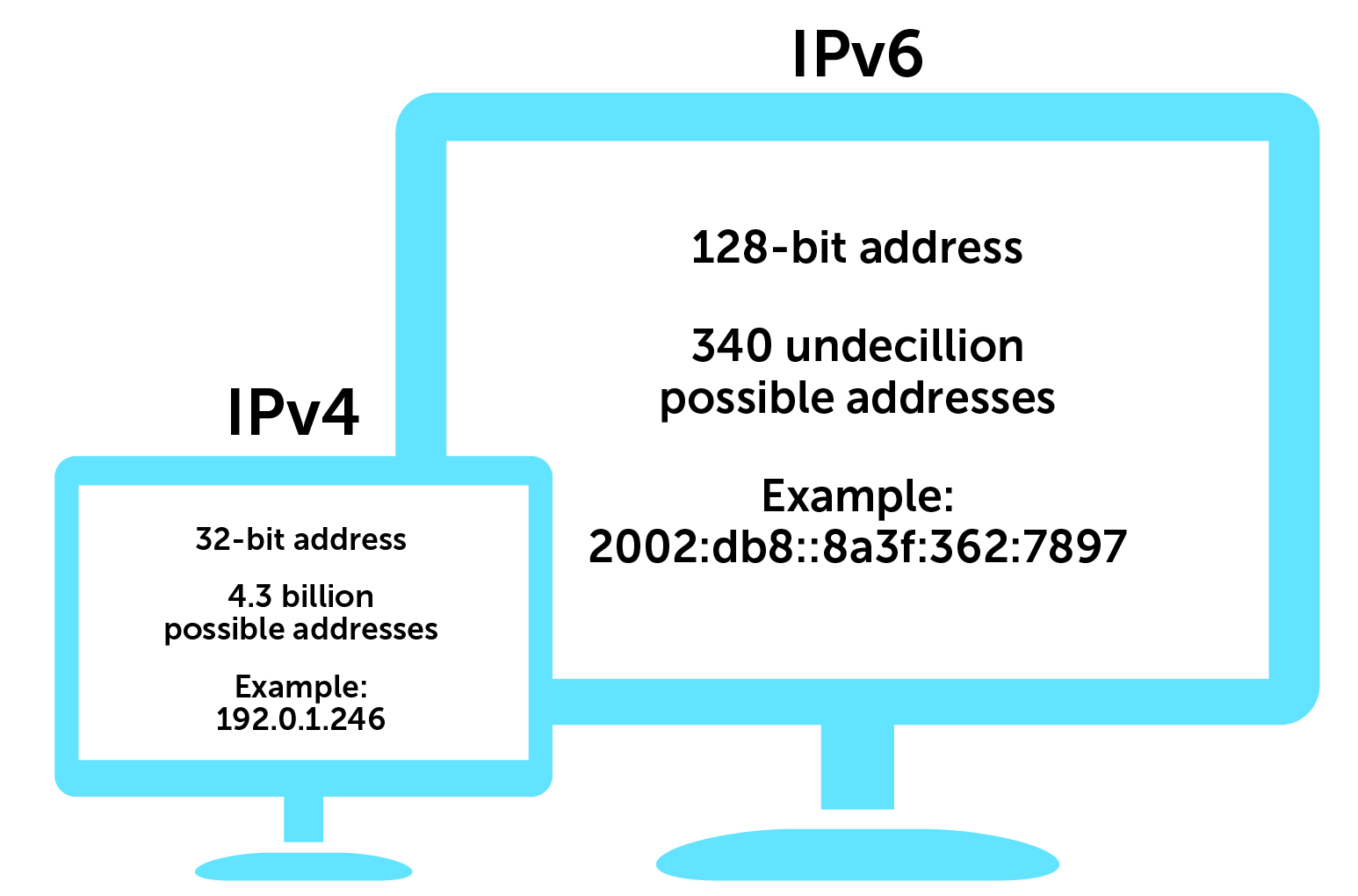
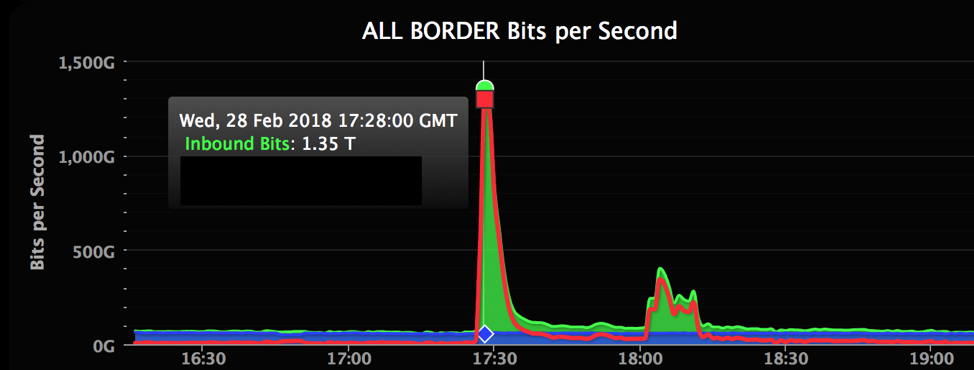
GitHub - burakkoray/Ipv6-Ddos-Attack-Protection: Ipv6 Ddos protection tool working under linux based machine
![PDF] An Experiment with DDoS Attack on NodeMCU12e Devices for IoT with T50 Kali Linux | Semantic Scholar PDF] An Experiment with DDoS Attack on NodeMCU12e Devices for IoT with T50 Kali Linux | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9f8a42ec37bb11cbef56b6dad90c5b249a3f20ac/4-Figure4-1.png)
PDF] An Experiment with DDoS Attack on NodeMCU12e Devices for IoT with T50 Kali Linux | Semantic Scholar
![PDF] Analysis of Entropy Based DDoS Attack Detection to Detect UDP Based DDoS Attacks in IPv 6 Networks | Semantic Scholar PDF] Analysis of Entropy Based DDoS Attack Detection to Detect UDP Based DDoS Attacks in IPv 6 Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3ceb3d37ae2ca9f7bbb18bff19e9c252e2dd250a/3-Figure1-1.png)
PDF] Analysis of Entropy Based DDoS Attack Detection to Detect UDP Based DDoS Attacks in IPv 6 Networks | Semantic Scholar

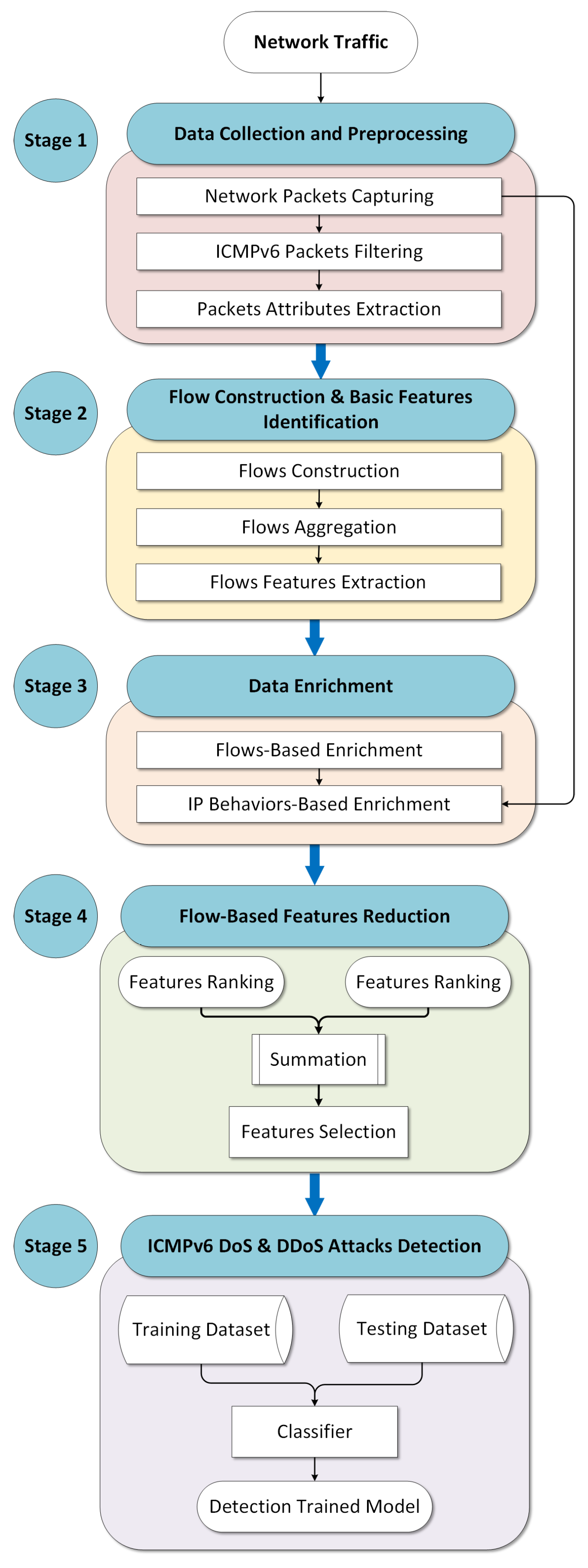
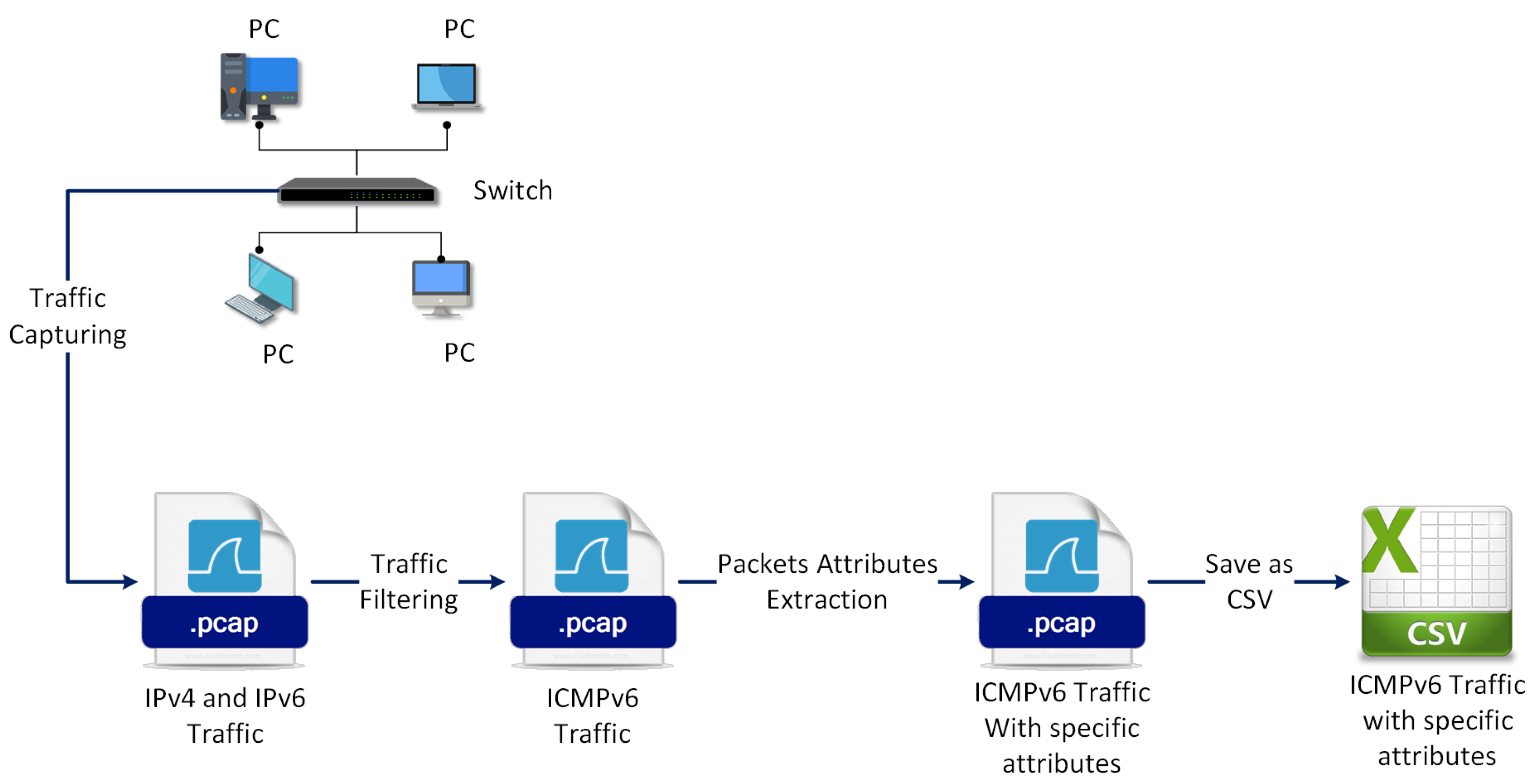
Classification of ICMPv6-based DoS and DDoS attacks defense mechanisms | Download Scientific Diagram
![PDF] An Experiment with DDoS Attack on NodeMCU12e Devices for IoT with T50 Kali Linux | Semantic Scholar PDF] An Experiment with DDoS Attack on NodeMCU12e Devices for IoT with T50 Kali Linux | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9f8a42ec37bb11cbef56b6dad90c5b249a3f20ac/3-Figure1-1.png)