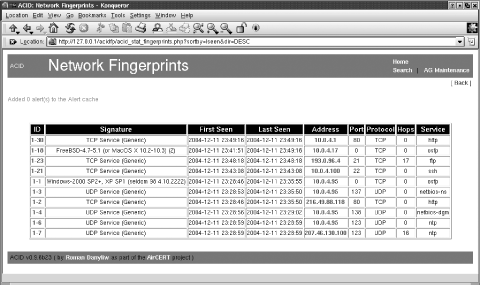
![PDF] A Machine-Learning-Based Tool for Passive OS Fingerprinting With TCP Variant as a Novel Feature | Semantic Scholar PDF] A Machine-Learning-Based Tool for Passive OS Fingerprinting With TCP Variant as a Novel Feature | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ca0589a1fad20446d5f185f9cf67c26e55775a9a/4-Figure2-1.png)
PDF] A Machine-Learning-Based Tool for Passive OS Fingerprinting With TCP Variant as a Novel Feature | Semantic Scholar
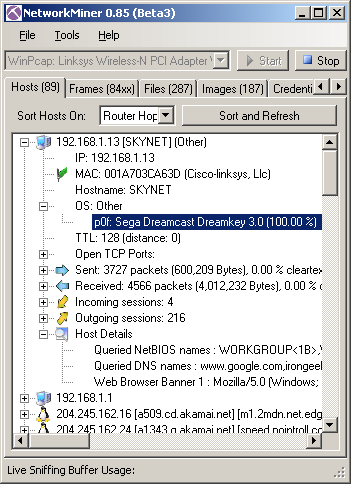
OSfuscate: Change your Windows OS TCP/IP Fingerprint to confuse P0f, NetworkMiner, Ettercap, Nmap and other OS detection tools
GitHub - cesarghali/OS-Fingerprinting: Operating system remote fingerprinting attack and detection tools

Explaining OS Fingerprinting. If a hacker can determine what type of… | by Arth Awasthi | FAUN — Developer Community 🐾

Hack Like a Pro: How to Use the New p0f 3.0 for OS Fingerprinting & Forensics « Null Byte :: WonderHowTo

ODA Open Digital Archive: A Machine Learning-based Tool for Passive OS Fingerprinting with TCP Variant as a Novel Feature

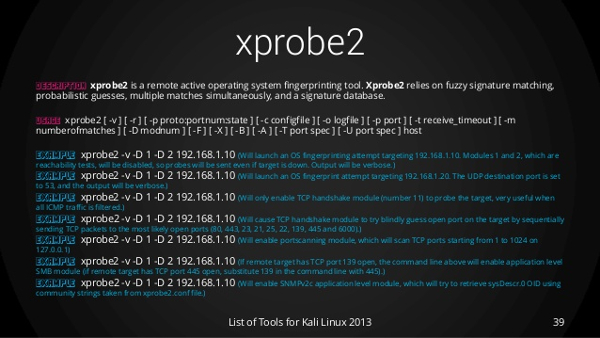
Active OS Fingerprinting - XPROBE2 Tutorial - Kali Linux 2022 - Ethical Hacking - CEH Basics - YouTube


![PDF] New Tool And Technique For Remote Operating System Fingerprinting | Semantic Scholar PDF] New Tool And Technique For Remote Operating System Fingerprinting | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/c3d78a5bf8ceac42e441732f4ac6fd307adf42f9/2-Figure1-1.png)